Encryption has discovered a spot in nowadays’s virtual global, through cultivating a tradition of safety and privateness. When the AES Encryption set of rules succeeded the Knowledge Encryption Same old as the worldwide same old for encryption algorithms in 2001, it fastened many shortcomings of its predecessor. It used to be noticed as the long run for encryption in day-to-day lifestyles packages. To this point, the Complex Encryption Same old has accomplished the objectives positioned right through its inception. And it has an extended solution to develop.
Why Was once the AES Encryption Set of rules important?
When the Knowledge Encryption Same old set of rules, often referred to as the DES set of rules, used to be shaped and standardized, it made sense for that era of computer systems. Going through nowadays’s computational requirements, breaking into the DES set of rules changed into more straightforward and quicker with annually, as noticed within the symbol underneath.
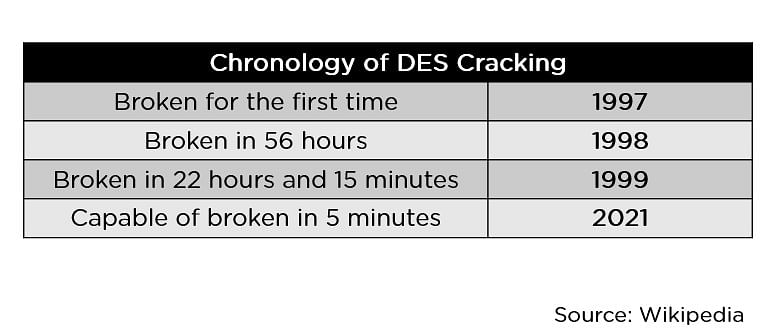
A extra tough set of rules used to be the will of the hour, with longer key sizes and more potent ciphers to damage into. They created the triple DES to mend this downside, however it by no means changed into mainstream on account of its fairly slower tempo. Thus, the Complex Encryption Same old got here into lifestyles to conquer this problem.
What’s the Complex Encryption Same old?
The AES Encryption set of rules (often referred to as the Rijndael set of rules) is a symmetric block cipher set of rules with a block/chew dimension of 128 bits. It converts those person blocks the use of keys of 128, 192, and 256 bits. As soon as it encrypts those blocks, it joins them in combination to shape the ciphertext.
It’s in line with a substitution-permutation community, often referred to as an SP community. It is composed of a sequence of connected operations, together with changing inputs with explicit outputs (substitutions) and others involving bit shuffling (diversifications).
On this instructional, you are going to undergo one of the crucial standout options that AES gives as a globally standardized encryption set of rules.
What are the Options of AES?
- SP Community: It really works on an SP community construction reasonably than a Feistel cipher construction, as noticed when it comes to the DES set of rules.
- Key Enlargement: It takes a unmarried key up right through the primary degree, which is later expanded to more than one keys utilized in person rounds.
- Byte Knowledge: The AES encryption set of rules does operations on byte information as a substitute of bit information. So it treats the 128-bit block dimension as 16 bytes right through the encryption process.
- Key Period: The choice of rounds to be performed relies on the period of the important thing getting used to encrypt information. The 128-bit key dimension has ten rounds, the 192-bit key dimension has 12 rounds, and the 256-bit key dimension has 14 rounds.
How Does AES Paintings?
To grasp the way in which AES works, you first want to find out how it transmits data between more than one steps. Since a unmarried block is 16 bytes, a 4×4 matrix holds the information in one block, with each and every mobile maintaining a unmarried byte of data.
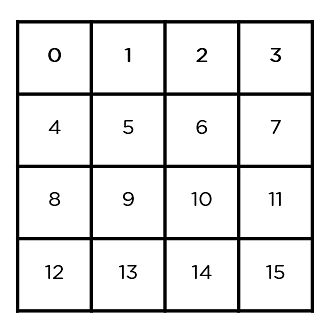
The matrix proven within the symbol above is referred to as a state array. In a similar fashion, the important thing getting used first of all is expanded into (n+1) keys, with n being the choice of rounds to be adopted within the encryption procedure. So for a 128-bit key, the choice of rounds is 16, without a. of keys to be generated being 10+1, which is a complete of eleven keys.
Steps to be adopted in AES
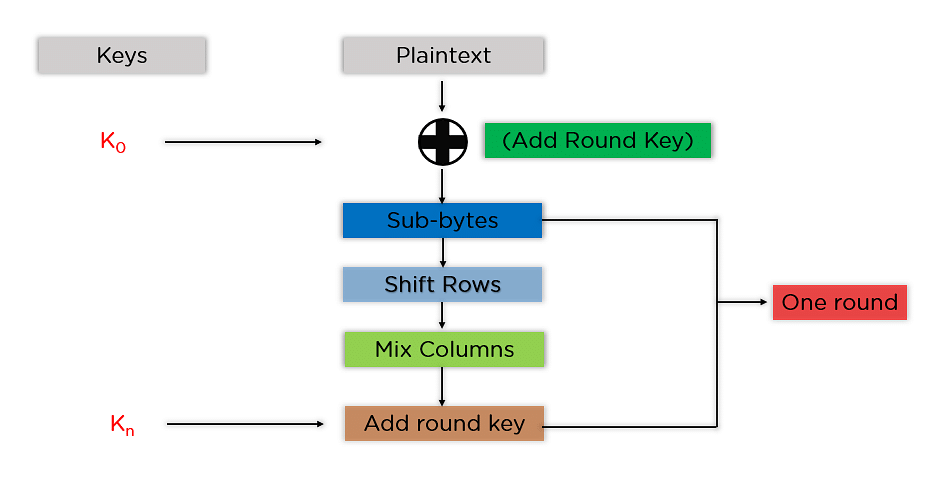
The discussed steps are to be adopted for each and every block sequentially. Upon effectively encrypting the person blocks, it joins them in combination to shape the overall ciphertext. The stairs are as follows:
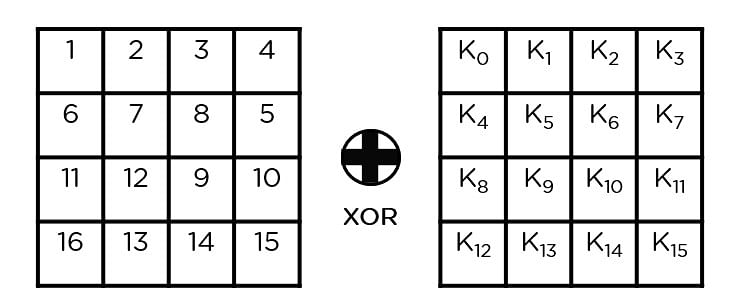
- Upload Spherical Key: You cross the block information saved within the state array thru an XOR serve as with the primary key generated (K0). It passes the ensuing state array on as enter to your next step.
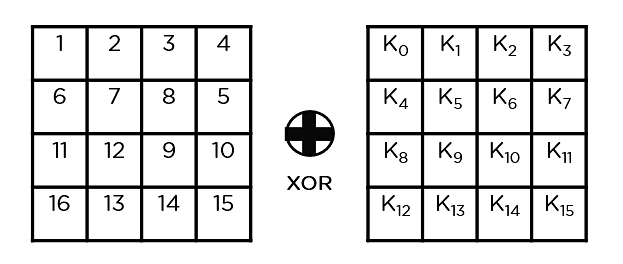
- Sub-Bytes: On this step, it converts each and every byte of the state array into hexadecimal, divided into two equivalent portions. Those portions are the rows and columns, mapped with a substitution field (S-Field) to generate new values for the overall state array.
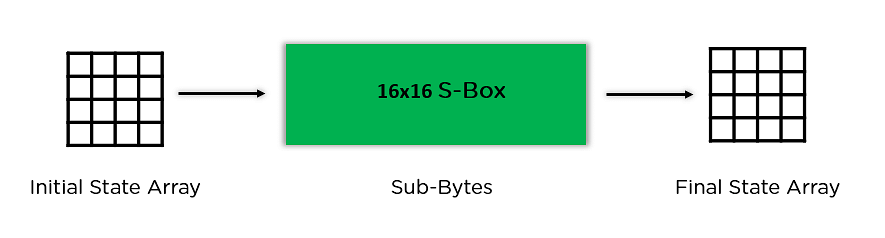
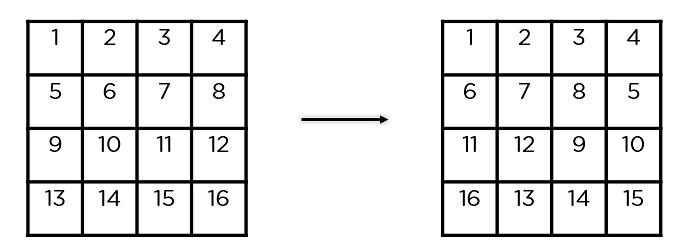
- Shift Rows: It swaps the row parts amongst each and every different. It skips the primary row. It shifts the weather in the second one row, one place to the left. It additionally shifts the weather from the 3rd row two consecutive positions to the left, and it shifts the final row 3 positions to the left.
- Combine Columns: It multiplies a relentless matrix with each and every column within the state array to get a brand new column for the following state array. As soon as all of the columns are multiplied with the similar consistent matrix, you get your state array for your next step. This actual step isn’t to be performed within the final spherical.
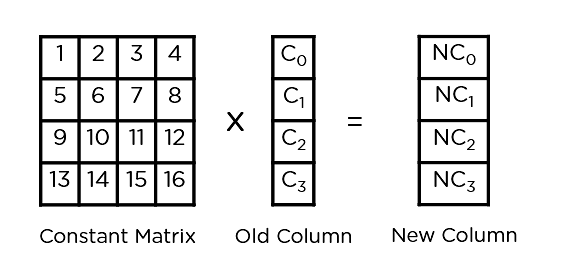
- Upload Spherical Key: The respective key for the spherical is XOR’d with the state array is acquired within the earlier step. If that is the final spherical, the ensuing state array turns into the ciphertext for the precise block; else, it passes as the brand new state array enter for the following spherical.
Now that you realize the fundamental steps had to move during the encryption process, perceive this case to practice alongside.
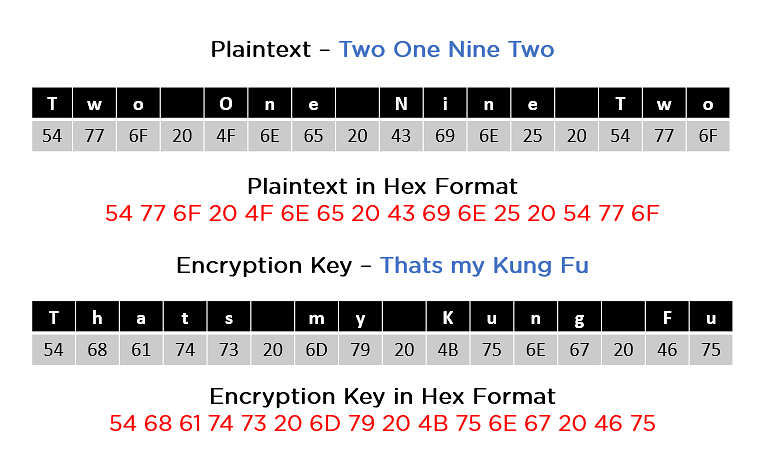
As you’ll see within the symbol above, the plaintext and encryption convert keys to hex layout sooner than the operations start. Accordingly, you’ll generate the keys for the following ten rounds, as you’ll see underneath.
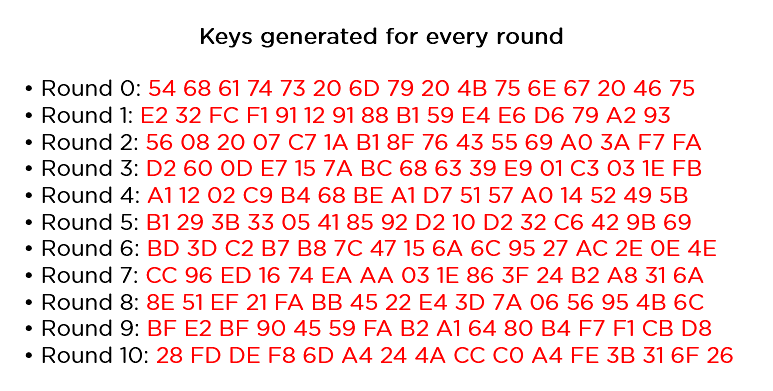
You want to practice the similar steps defined above, sequentially extracting the state array and passing it off as enter to the following spherical. The stairs are as follows:
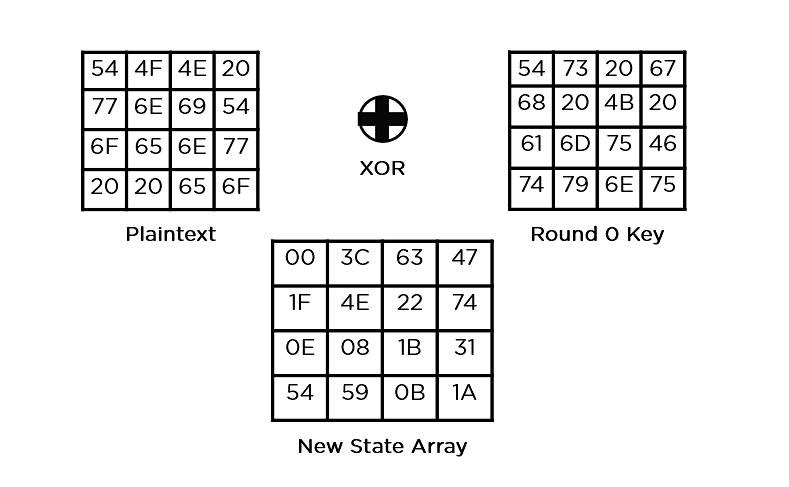
- Sub-Bytes: It passes the weather thru a 16×16 S-Field to get an absolutely new state array.
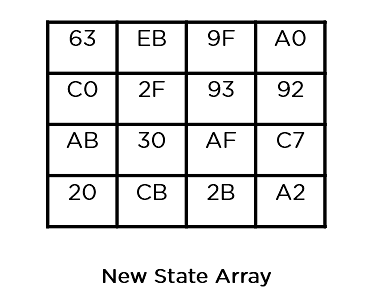
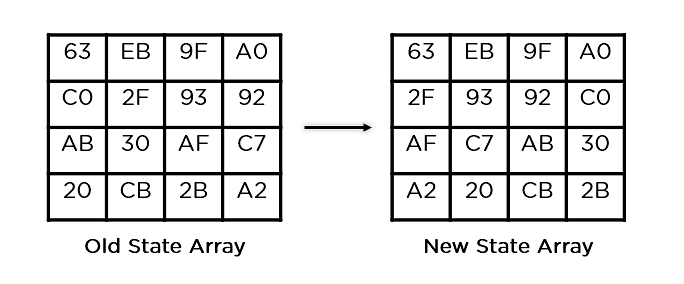
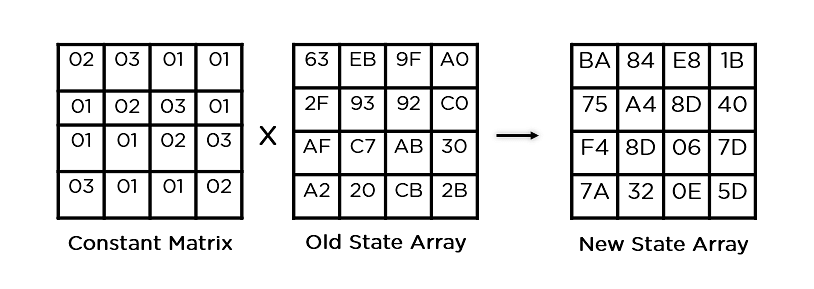
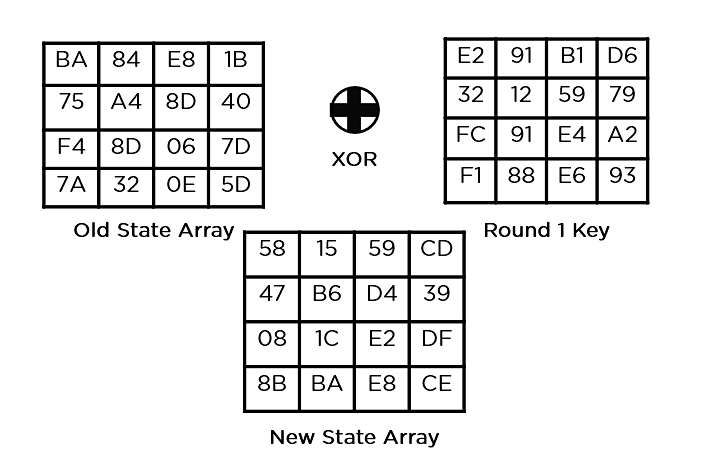
This state array is now the overall ciphertext for this actual spherical. This turns into the enter for the following spherical. Relying at the key period, you repeat the above steps till you entire spherical 10, and then you obtain the overall ciphertext.
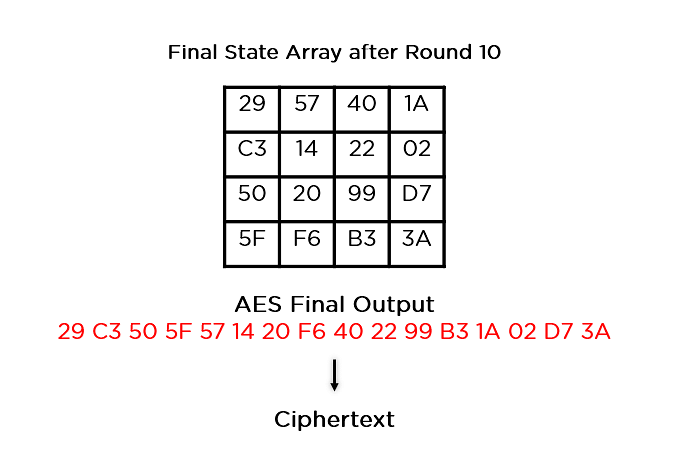
Now that you know how AES works, undergo one of the crucial packages of this encryption set of rules.
What Are the Packages of AES?
The packages of the AES Encryption set of rules are as follows:
- Wi-fi Safety: Wi-fi networks are secured the use of the Complex Encryption Same old to authenticate routers and purchasers. WiFi networks have firmware tool and entire safety techniques in line with this set of rules and are actually in on a regular basis use.
- Encrypted Surfing: AES performs an enormous function in securing web page server authentication from each consumer and server finish. With each symmetric and uneven encryption getting used, this set of rules is helping in SSL/TLS encryption protocols to all the time browse with the maximum safety and privateness.
- Normal Report Encryption: Except company must haves, AES could also be used to switch recordsdata between buddies in an encrypted layout. The encrypted data can prolong to talk messages, circle of relatives photos, felony paperwork, and many others.
- Processor Safety: Many processor producers allow hardware-level encryption the use of the likes of AES encryption to reinforce safety and save you meltdown screw ups, amongst different low-profile dangers.
Now that you just realized concerning the packages of AES encryption, check out its upgrades over its predecessor, the DES encryption set of rules.
Variations Between AES & DES
DES Set of rules |
AES Set of rules |
|
Key Period – 56 bits |
Key Period – 128, 192, 256 bits |
|
Block Dimension – 64 bits |
Block dimension – 128 bits |
|
Mounted no. of rounds |
No. of rounds depending on key period |
|
Slower and no more protected |
Quicker and extra protected |
FAQs
1. Is AES encryption protected?
AES encryption is protected; on the other hand, its safety varies in keeping with its variants. As an example, the use of brute-force strategies, the 256-bit is just about impenetrable, whilst the 52-bit DES key can also be cracked in not up to an afternoon.
2.Is AES the most efficient encryption way?
On account of its key period choices, AES encryption stays your best choice for securing communications. The time required to crack an encryption set of rules is without delay associated with the period of the important thing used, i.e., 128-bit, 192-bit, and 256-bit.
3. What’s AES encryption used for?
AES is carried out in {hardware} and tool international to encrypt delicate information. This can be a symmetric block cipher very important for presidency pc safety, digital information coverage, and cybersecurity.
4. Which is best: RSA or AES?
RSA is significantly slower and extra computationally in depth than AES. RSA has to maintain huge numbers and calculations, which makes it slower. AES is thought of as protected towards research with quantum computer systems and is in most cases utilized by more than a few organizations.
5. Is AES unfastened to make use of?
AES is to be had at no cost, and any individual can use it. Regardless that a number of nations practice export restrictions, it’s an open same old this is unfastened to make use of for any personal, public, non-commercial, or advertisement use.
6. What’s AES?
Complex Encryption Same old is a symmetric block cipher selected through america executive. It converts the person blocks the use of other keys. It is likely one of the best possible encryption protocols to be had, letting any individual experience their day-to-day on-line actions with out disruption.
How Can Simplilearn Assist You?
With this, you have got noticed the affect AES Encryption has at the world degree, with many techniques wanting a protected channel of authentication as DES collapsed. With many bases to hide in cybersecurity, cryptography is likely one of the maximum the most important sides, even supposing a number of different subjects are very important to excel as a cybersecurity skilled.
Simplilearn gives a “Cybersecurity Skilled” route designed to equip you with all of the abilities important to begin or advertise your profession in cybersecurity. It doesn’t have any educational pre-requirements, and the introductory module will get ready freshmen for the route forward. Coaching for extremely sought-after certifications like CompTIA Safety+, CEH, CISM, and CISSP is at the leading edge of this route, getting ready you for the most efficient jobs being introduced within the {industry}.
Change into your cybersecurity profession and turn into an industry-ready skilled through enrolling in our Complex Government Program in Cybersecurity nowadays.
Conclusion
This instructional explores the will for AES Encryption, its foundation and technique of encryption, all of the method as much as its packages, and an instantaneous comparability with the DES set of rules. Hope this instructional has been of price to you.
In case you are having a look to be informed additional on encryptions, cryptography and different elementary ideas and talents in cybersecurity, Simplilearn’s Complex Government Program In Cyber Safety program will have to be a really perfect have compatibility for you. This program covers all of the elementary and complex sides of cybersecurity and gives you the best job-ready coaching you want to turn into a world-class cybersecurity skilled nowadays. Discover this system nowadays.
Do you have got any questions for us referring to this AES encryption instructional? Please don’t hesitate to say them within the remark segment of this instructional, and we’d be at liberty to have our mavens resolution them for you.
supply: www.simplilearn.com












