TCS is among the maximum sought-after corporations by means of IT execs owing to its collaborative and supportive tradition and international reputation as an international chief within the IT sector. Once a year TCS supplies numerous activity alternatives for candidates in quite a lot of fields. To nail the chance at TCS, candidates will have to brace up for essentially the most difficult TCS interview questions with strategic preparation and constant observe. Repeatedly requested interview questions given under will take a look at your cognitive and verbal exchange abilities.
TCS Interview Questions and Solutions
1. Outline socket programming and point out the advantages and disadvantages of java sockets.
Socket programming is a kind of programming that permits for verbal exchange between two units. This kind of verbal exchange is continuously completed over a community, such because the Web. Socket programming can be utilized to create quite a few programs, corresponding to internet servers, chat shoppers, and extra.
Socket programming is some way of the usage of the web to attach two or extra units. This can also be completed thru a stressed connection, corresponding to an Ethernet cable, or a wi-fi connection, corresponding to Wi-Fi.
Advantages of Java Sockets:
Java Sockets are used with a purpose to permit two programs to keep up a correspondence over the web. In easy phrases, they give you the skill to attach two units and make allowance them to keep up a correspondence with every different. There are lots of advantages to the usage of Java Sockets which come with: the power to construct community programs briefly, the truth that they’re platform self sufficient, they usually supply a top point of safety. This paper will discover every of those advantages in additional intensity.
Whilst Java sockets don’t seem to be the one form of socket to be had to a developer, they’re by means of some distance essentially the most frequently used. The most important reason why for that is that they provide a top point of abstraction. Which means that a programmer does no longer have to fret concerning the underlying communications protocol. Some other good thing about the usage of Java sockets is that they enable for the introduction of reusable elements.
Drawbacks of Java Sockets:
Java sockets, like every other community protocol, have their disadvantages. As an example, Java sockets are slower than different protocols as a result of their use of UDP. Java sockets are an invaluable solution to ship knowledge between programs and servers, however there are some drawbacks. First, verbal exchange can also be sluggish as a result of Java makes use of TCP as an alternative of UDP. Moreover, Java does no longer improve synchronous verbal exchange, so knowledge can also be misplaced if the 2 programs don’t seem to be responding to one another.
2. Outline IPsec and point out its elements.
IPsec is a safety protocol that makes use of cryptographic safety products and services to offer protection to communications over an Web Protocol (IP) community. IPsec makes use of two elements to offer safety: Authentication Header (AH) and Encapsulating Safety Payload (ESP). AH authenticates the sender and the receiver of the knowledge, while ESP encrypts the knowledge to offer protection to it from being learn by means of unauthorized customers.
IPsec is a protocol that gives authentication and encryption for Web Protocol communications. It helps network-level peer authentication, knowledge integrity, knowledge confidentiality (encryption), and replay coverage. IPsec helps delivery and tunnel modes and is obligatory to put in force for all IP implementations.
IPsec is a community layer protocol that gives knowledge confidentiality, knowledge integrity, knowledge starting place authentication, and knowledge anti-replay provider. IPsec makes use of cryptographic safety products and services to offer protection to verbal exchange over untrusted networks such because the Web. The cryptographic algorithms and protocols utilized by IPsec were designed to give you the following safety products and services:
Confidentiality: This provider guarantees that knowledge can’t be learn by means of somebody instead of licensed receivers.
Information integrity: This provider guarantees that transmitted knowledge has no longer been altered whatsoever.
3. What do you imply by means of subnet masks?
The subnet masks tells the pc which a part of the IP deal with is the community section and which section is the host section. The subnet masks is used to resolve whether or not a given IP deal with is at the similar community as the pc this is inquiring for the guidelines. If the pc inquiring for the guidelines has the similar subnet masks as the pc that has the guidelines, then the pc inquiring for the guidelines can think that the guidelines is at the similar community.
Subnetting is the method of dividing a community into smaller subnets, every with its personal distinctive IP deal with and subnet masks. Subnetting means that you can higher regulate visitors glide and preserve IP addresses. It additionally means that you can section your community into other safety zones. As an example, you have to create a separate subnet in your DMZ (Demilitarized Zone) and some other subnet in your inner community.
4. Outline NAT.
NAT stands for Community Cope with Translation. When a pc is hooked up to the web, the pc’s community card must know the way to speak to the opposite computer systems on the net. That is completed by means of translating the pc’s public IP deal with (which is simple to bear in mind, like www.google.com) into the addresses that the web makes use of (like 192.168.1.1). NAT is vital as a result of there are such a lot of other networks on the planet and each and every certainly one of them makes use of a unique IP deal with.
5. What do by means of piggybacking?
Piggybacking is while you use any individual else’s content material to improve your personal argument. As an example, when you’re debating a subject matter and you utilize a statistic that your opponent has utilized in a prior argument, you’re piggybacking. The issue with piggybacking is that it may be unfair. In case your opponent is the usage of a statistic that you simply don’t learn about, you may no longer be capable of refute it.
Piggybacking is a solution to get advantages from products and services you utilize with out in truth having to make use of their supplier. As an example, when you use Gmail, you’ll be able to piggyback on their electronic mail garage in order that your electronic mail remains in Gmail as an alternative of being despatched on your private electronic mail account.
6. What’s database schema and its sorts?
A database schema is the structure of a database, and it comprises the group of knowledge and the relationships between them. There are 3 primary kinds of schema: bodily, logical, and consider. A bodily schema is the real database structure, whereas a logical schema is a illustration of the knowledge within the database. A view schema is a subset of the database this is used for a selected goal.
A database schema is the construction or structure of a database. There are 3 primary kinds of schema: relational, object-oriented, and XML. A relational schema is a desk that lists the fields in a database and the relationships between them. An object-oriented schema is a diagram that presentations the gadgets in a database and the relationships between them.
7. Differentiate clustered and non-clustered indexes.
Clustered indexes are nice for ensuring your knowledge is readily and simply discovered, whereas non-clustered indexes can also be extra environment friendly when you best wish to glance up a unmarried file.
8. What’s around time out time?
Spherical time out time is the time it takes for a knowledge packet to make a around time out from the supply to the vacation spot and again. Spherical time out time is the most important metric in laptop networking as a result of it may be used as a measure of community latency.
The round-trip time is measured by means of sending a packet, looking ahead to its go back, after which repeating the method.
9. What’s Ping?
Ping is a community visitors size instrument this is used to diagnose problems with a community. This is a community instrument that can be utilized to test whether or not a tool is reachable. Whilst you ping a tool, you ship a packet of knowledge to it and look ahead to a reaction. If the tool isn’t responding, it may well be down or it may well be busy. Whilst you ping a tool, you’ll be able to use the ping command to test whether or not the community is operating and whether or not the tool is reachable.
10. Record some issues about SLIP.
SLIP is a pc protocol utilized in point-to-point serial connections. It stands for Serial Line Web Protocol. It used to be as soon as frequently used to attach private computer systems by the use of phone traces the usage of a modem however has been in large part changed by means of more recent protocols corresponding to PPP. SLIP used to be outlined in RFC 1055.
11. What do about Ethernet?
Ethernet is a pc networking era usual for Native Space Networks (LANs). It used to be in the beginning advanced within the Nineteen Seventies by means of Bob Metcalfe and others running at Xerox PARC. Ethernet makes use of a bus or famous person topology and helps knowledge switch charges of 10 Mbit/s, 100 Mbit/s, 1 Gbit/s, and 10 Gbit/s. Ethernet is standardized by means of IEEE 802.3. It has in large part changed competing stressed LAN applied sciences corresponding to token rings and FDDI.
Ethernet is among the maximum commonplace laptop networking applied sciences in use these days. This is a native space community (LAN) era that gives a solution to attach computer systems and different units in a restricted geographical space. Ethernet makes use of a unique roughly cable and connectors, and it operates at a far upper pace than different LAN applied sciences.
12. What do you imply by means of tunnel mode in networking?
Networks are necessary for permitting knowledge to glide between two or extra units. Tunnel mode in networking lets in for extra environment friendly use of networks by means of breaking knowledge into smaller packets and sending them thru a tunnel.
13. Write concerning the RSA set of rules in short.
RSA is a calculation for public-key cryptography this is in most cases used in digital trade. It used to be created in 1977 by means of Ron Rivest, Adi Shamir, and Len Adleman. The calculation depends upon the way in which that it’s really difficult to issue an enormous quantity this is the results of two indivisible numbers. RSA is used in a large collection of utilizations, together with electronic mail, file sharing, and protected correspondence.
14. What’s cyclomatic complexity in a device program?
Cyclomatic complexity is a measure of the selection of traces of code in a program. The upper the cyclomatic complexity, the extra complicated this system. Device with top cyclomatic complexity is tougher to learn and take care of.RSA is an set of rules for public-key cryptography this is broadly utilized in digital trade. RSA used to be created in 1977 by means of Ron Rivest, Adi Shamir, and Len Adleman. The set of rules is in response to the truth that it is vitally tough to issue a big quantity that’s the product of 2 high numbers. Give an instance of a time while you did not discover a computer virus in black field trying out however came upon it in white field trying out.
15. Give an instance of a time while you didn’t discover a computer virus in Black Field trying out however came upon it in white field trying out.
Black field trying out is a technique of trying out device the place the inner construction of the code being examined isn’t recognized. In this sort of trying out, the tester is best occupied with the inputs and outputs of the device beneath take a look at. Black field trying out is often referred to as behavioral trying out. White field trying out, however, is a technique of trying out device the place the inner construction of the code being examined is understood.
16. What’s slice splicing in device trying out? What are its two sorts?
Slice splicing is a kind of black field trying out the place the tester best has get admission to to the inputs and outputs of the device beneath take a look at. There are two kinds of slice splicing: complete and partial. Complete slice splicing offers the tester entire get admission to to all inputs and outputs, whereas partial slice splicing best offers the tester get admission to to a subset of inputs and outputs. I take into account a time when I used to be doing black field trying out and I did not discover a computer virus.
17. Differentiate between AWT and Swing in java.
AWT (Summary Windowing Toolkit) is a Java GUI toolkit that gives a collection of interfaces that permit builders to create consumer interfaces. Swing is some other Java GUI toolkit that gives a extra user-friendly interface and is well-liked amongst builders who’re new to Java. As you’ll be able to see, AWT is extra conventional and Swing is extra user-friendly. It supplies a wealthy set of options for developing graphical consumer interfaces (GUIs). Swing is a more moderen windowing surroundings that used to be advanced in particular for the Java platform.
18. Provide an explanation for reminiscence leak in C++. How are you able to steer clear of it?
When programming in C++, programmers must be cautious to steer clear of reminiscence leaks. A reminiscence leak is when a program allocates reminiscence however does no longer deallocate it correctly, which may end up in this system the usage of an increasing number of reminiscence over the years. To steer clear of reminiscence leaks, programmers will have to be sure you correctly deallocate reminiscence when they’re completed the usage of it.
Reminiscence leaks are a commonplace downside in C++ programming. They happen when the reminiscence that has been allotted isn’t correctly deallocated. This may end up in wasted reminiscence and, in some circumstances, to program crashes. There are a number of tactics to steer clear of reminiscence leaks.
19. What do by means of a command-line argument in C?
Command-line arguments are necessary in C++. They enable programmers to specify which purposes to run and the way they will have to be performed. As an example, when you sort “./myprogram -arg 1”, this system will run and cross the argument “1” to the myprogram serve as.
When the usage of the command line in C++, programmers want to concentrate on the various kinds of arguments that they may be able to cross to a program. There are 3 primary kinds of arguments: positional arguments named arguments, and command-line arguments. Positional arguments are those which are indexed at the command line. They’re those you sort in sequentially.
20. What do you imply by means of concurrency regulate?
Concurrency regulate is necessary in any utility, however it’s specifically the most important in C++ methods. When more than one threads are working in parallel, it is very important make certain that the code is written in order that it may be performed asynchronously. Doing so lets in this system to deal with extra concurrent requests and steer clear of One of the crucial commonplace issues that may happen when more than one threads are working concurrently.
21. What do about SQL correlated subqueries?
SQL-correlated subqueries generally is a tough instrument for exploring knowledge. They will let you question knowledge this is associated with the knowledge you might be already querying. This can also be helpful when you need to seek out knowledge this is associated with a selected column on your desk.
22. Outline a checkpoint in a database control device, and when it eventuates.
A checkpoint in a database control device is an match this is precipitated when the database reaches a undeniable level in its efficiency historical past. With a purpose to save you the database from changing into risky, this checkpoint will have to be carried out at least one time each and every six months.
It’s the most important match that are meant to be deliberate for and performed once imaginable. There are a variety of the explanation why this will have to occur, and crucial one is to make certain that the knowledge within the database is proper.
23. What are the 2 integrity laws in a database control device?
In a database control device, two integrity laws will have to be adopted: the ACID rule and the Atomicity rule. The ACID rule states that any alternate to an object will have to be made atomically, because of this that the entire knowledge concerning the object will have to be modified on the similar time. This guarantees that the database stays constant and dependable.
24. What precisely are macros? What are the advantages and disadvantages?
A macro is a series of instructions that you simply workforce in combination as a unmarried command to perform a job that may in a different way be too tough or time-consuming. By way of the usage of a chain of instructions to automate a job, you’ll be able to save a fantastic quantity of effort and time when acting commonplace duties corresponding to formatting textual content, or complicated duties corresponding to construction charts that comprise a large number of elements. You’ll use the Macro Recorder to robotically generate macros for commonplace duties, and edit the recorded macros to fine-tune them for maximum efficiency. You’ll additionally write macros by means of the usage of Visible Fundamental for Packages (VBA) code.
Macros generally is a useful instrument for automating duties, however pay attention to their drawbacks. As an example, macros can build up the workload of your laptop as a result of they run as a background job. Moreover, macros can soak up a large number of reminiscence, so you could wish to stay observe of ways a lot house they’re the usage of.
25. What’s the distinction between JDK and JRE?
The Java Construction Package (JDK) is a device building surroundings for creating Java programs and elements. Java is a general-purpose laptop programming language that can be utilized to increase programs for quite a lot of platforms together with desktops, servers, cell phones, private virtual assistants, embedded programs, recreation consoles, set-top packing containers, and network-attached garage units. Against this, the JRE is the runtime surroundings for Java programs. It accommodates a Java Digital Device (JVM), category libraries, and different supporting recordsdata.
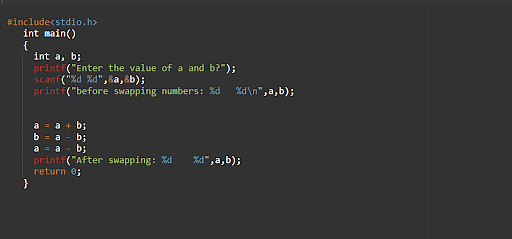
26. What’s the way to switch two numbers with out the usage of a 3rd variable?
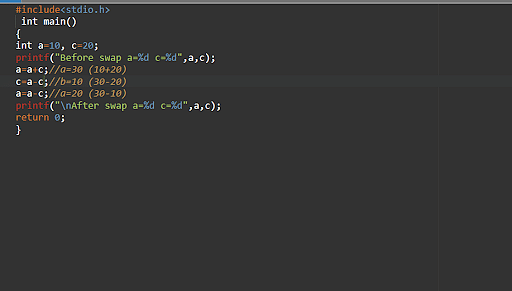
Output –
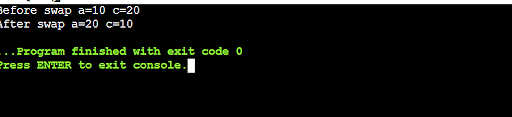
27. Point out the code to opposite a given quantity the usage of command line arguments.
There are lots of other ways to opposite a bunch the usage of the command line arguments. As an example, the next code reverses a bunch the usage of the argv variable: argv[1] – argv[0] . In a different way to opposite a bunch the usage of the command line arguments is the usage of the reversed() serve as. reversed() takes two arguments: the quantity to opposite and the string to make use of because the opposite string.
28. What is supposed by means of cycle stealing?
Cycle stealing is a technique of the usage of additional clock cycles to accomplish different operations that don’t seem to be associated with the principle job. In a device with more than one units, every tool could also be given a undeniable selection of clock cycles to accomplish its job. If one tool isn’t the usage of all of its clock cycles, some other tool can use the additional clock cycles, or ‘scouse borrow’ them.
29. Point out the 2 ideas of swapping within the context of OS? How does swapping assist in higher reminiscence control?
Swapping is the method of shifting blocks of knowledge from one location to some other in order that the knowledge can also be accessed extra simply. Swapping is a commonplace observe in running programs, specifically when coping with reminiscence control. Swapping is helping to make stronger reminiscence control by means of permitting the OS to raised make the most of the to be had reminiscence.
There are two ideas of swapping within the context of OS: procedure swapping and reminiscence swapping. Procedure swapping lets in the running device to transport processes from primary reminiscence to disk reminiscence and vice versa. This is helping in higher reminiscence control as inactive processes can also be moved to a disk reminiscence, liberating up house in the principle reminiscence. Reminiscence swapping, however, lets in the running device to transport blocks of reminiscence from primary reminiscence to disk reminiscence and vice versa.
30. What’s the RR Scheduling Set of rules in OS?
The RR Scheduling Set of rules is a scheduling set of rules this is utilized in running programs to agenda processes. The set of rules is designed to paintings with processes that experience equivalent precedence. The set of rules works by means of giving every procedure a time slice, which is a unit of time that the method is authorized to run. The time slice is normally set to a price this is sufficiently small so that each one processes get a fair proportion of the CPU time.
31. What are interrupts?
Interrupts are a kind of sign that may be despatched to a procedure to signify that an match has came about. When an interrupt is distributed to a procedure, the method is claimed to be interrupted. The method can then deal with the development that has came about.
Interrupts are indicators which are despatched to the CPU by means of {hardware} or device units. Those indicators inform the CPU to forestall what it’s doing and get started working a unique procedure. Interrupts can also be brought about by means of such things as a keyboard or mouse getting used, or a timer working out. When an interrupt happens, the CPU saves the state of the present procedure and begins working the interrupt handler.
32. Provide an explanation for the capability of the connected checklist.
The final node within the checklist has a hyperlink to the primary node. Each and every part within the connected checklist is hooked up to the following part within the checklist. The weather in a connected checklist don’t seem to be saved in contiguous reminiscence places. The connected checklist can be utilized to retailer a series of knowledge parts.
Examples:
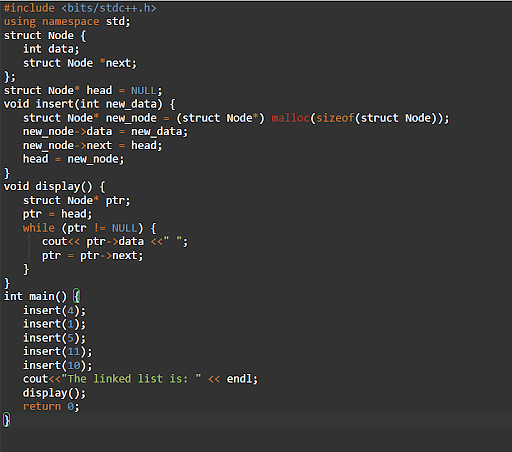
Output:
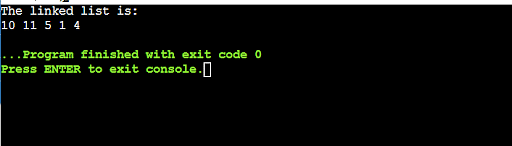
33. Point out the 4 fundamental ideas of OOPS.
Object Orientated Programming is an effective way to increase complicated methods. It is helping in creating the device by means of dividing it into gadgets.
The 4 fundamental ideas of OOPS are
- Encapsulation:
- Inheritance:
- Polymorphism:
- Abstraction
34. What’s inheritance?
Inheritance lets in programmers to create new categories that inherit the attributes and strategies of current categories. This will save a large number of effort and time when developing device.
Inheritance is the power of 1 category to inherit the attributes and behaviour of some other category. This turns out to be useful for developing hierarchies of categories, the place every subclass inherits the attributes and behaviour of its superclass. Inheritance is an impressive instrument that can be utilized to create tough and dependable device.
35. What’s the manner of inheriting the variable of 1 category to every other category?
Inheritance lets in programmers to create new categories that inherit the attributes and strategies of current categories. This will save a large number of effort and time when developing device. Inheritance is an impressive instrument that can be utilized to create tough and dependable device. The conduct of its superclass.
Inheritance can also be completed in certainly one of two tactics: by means of the usage of the @inherit annotation, or by means of the usage of the extends key phrase. The @inherit annotation is the extra commonplace of the 2 and lets in any category to inherit the variables and strategies of some other category. The extends key phrase is much less commonplace however lets in a category to inherit the variables and strategies of some other category, in addition to the category itself. Inheritance is an impressive instrument that can be utilized to create tough and dependable device.
36. What’s polymorphism?
Polymorphism is the power of a category to act another way relying on what form of object it’s forged to. This can also be helpful when writing device, because it lets in various kinds of gadgets to be treated in the similar method. As an example, a programmer may wish to permit a consumer to enter textual content in both a textual content field or a textual content space box. By way of the usage of polymorphism, the programmer can write code that handles each kinds of enter as it should be.
37. What are the various kinds of inheritance?
Inheritance is the passing of belongings, titles, money owed, rights, and tasks from one technology to the following.
There are 3 kinds of inheritance:
1. Felony inheritance: This kind of inheritance is given by means of regulation and no longer by means of will. It additionally does no longer rely on any situation.
2. Testamentary inheritance: This kind of inheritance can also be given in a will.
3. Intestate succession: The one that dies with out a will or testomony has their belongings handed to their members of the family in line with the foundations specified by state regulation.
38. Differentiate between categories and interfaces.
Categories are a elementary construction in object-oriented programming. They’re very similar to interfaces in that they outline how a category behaves, however they’ve some necessary variations. First, categories outline the kind of object that they devise, whereas interfaces don’t. Which means that categories can be utilized to create gadgets that don’t exist in the actual international, corresponding to interface categories.
39. What’s the device building existence cycle?
The device building existence cycle (SDLC) is a framework that gives a construction for figuring out the stairs which are required to increase a work of device. It is usually used so as to measure the growth of a device building challenge. The SDLC can be utilized in several tactics, however it’s generally divided into six other levels: necessities accumulating, design, implementation, trying out, deployment, and upkeep. Step one within the SDLC is necessities accumulating.
40. Outline the normalization of databases, joins, and keys.
Database normalization is a knowledge design method used to arrange a database into tables and columns. The principle concept of normalization is to separate up your knowledge into more than one tables and to outline relationships between them. This strategy of normalization normally leads to a extra environment friendly and efficient database design. Normalization is continuously used when designing relational databases.
With a purpose to take care of knowledge consistency and scale back redundancy, databases are normalized. This comes to breaking down tables into their smallest elements and best storing comparable knowledge in one desk. Redundancy may end up in inconsistency, for instance, if an deal with is saved in a couple of position and one reproduction is up to date however the different isn’t. Normalization additionally comes to the usage of keys, which might be distinctive identifiers for every file, and joins, which might be used to narrate knowledge in several tables.
41. What are loops?
Loops are used to copy a block of code a given selection of instances or till a undeniable situation is met. The commonest form of loop is the for loop, which is used to iterate over a series of values. As an example, a for loop can be utilized to print every part in a listing. Different kinds of loops come with the whereas loop, which executes a block of code so long as a situation is right, and the do-while loop, which executes a block of code at least one time sooner than checking the situation.
In laptop programming, a loop is a series of directions this is frequently repeated till a undeniable situation is reached. As an example, a programmer may use a loop to test every personality in a string to look if this is a letter or a bunch. Loops are continuously used when a program wishes to copy an motion a collection selection of instances. In some programming languages, the programmer can set the selection of instances the loop will run.
42. Provide an explanation for Joins, Perspectives, Normalization, and Triggers.
Joins are used to mix tables right into a unmarried desk. Perspectives will let you see the knowledge in two or extra tables on the similar time. Normalization is the method of constructing knowledge in a desk constant in order that it’s simple to know and use. Triggers are used to robotically run a chain of instructions when a undeniable situation is met.
Joins, perspectives, normalization, and triggers are all necessary in terms of database design. Joins permit two tables to be mixed right into a unmarried desk, perspectives permit a database consumer to look knowledge from one desk in a unique desk, normalization makes certain knowledge is formatted as it should be, and triggers permit a program to take explicit movements when a selected match happens.
43. Record other benefits of DBMS.
The benefits of DBMS are –
- DBMSs are designed to be fault-tolerant, because of this that if a {hardware} or device failure happens, it may well proceed running with none knowledge loss.
- DBMSs are designed to be scalable and will develop with the scale and complexity of the group.
- DBMSs supply an ordinary method of having access to knowledge throughout all programs, which is necessary for organizations that wish to proportion knowledge amongst other departments or programs.
- DBMSs supply a very easy method of managing adjustments in garage capability by means of including extra disks or changing disks with better ones with out disrupting the operation of different portions of the device.
44. What’s a Database Control Gadget?
A database control device (DBMS) is a device device that gives an arranged construction for storing, retrieving, and manipulating knowledge. DBMSs can also be present in quite a few programs, together with trade, medical, and engineering fields. DBMSs are very important for managing massive units of knowledge.
45. What are conditional statements?
Conditional statements are broadly utilized in laptop programming because it is helping programmers to regulate the collection of execution of methods in response to some given prerequisites. If the situation evaluates to true, then the corresponding true block code is performed, in a different way, the false block code is performed. The if…else remark is used once we wish to execute a undeniable remark or a block of statements when a selected situation is glad; and execute some other remark or some other block of statements when the situation isn’t glad. Within the else block, we will write a default situation.
46. Differentiate between the overseas key and reference key?
A reference secret is a column or set of columns in a desk this is used to spot the connection between other entities in a database. A overseas secret is a column or set of columns which are used to ascertain and put in force a hyperlink between the knowledge in two tables. To ensure that a overseas key to be created, it will be significant {that a} number one or distinctive key exists within the desk. In SQL, a overseas key can be utilized to stop the deletion of knowledge this is referenced by means of different knowledge within the database.
47. Record the variations and similarities between C and C++?
C is a structured programming language advanced by means of Dennis Ritchie in 1972. It used to be designed to permit programmers to write down device that had to be environment friendly and transportable. C++ used to be advanced by means of Bjarne Stroustrup in 1979. This is a superset of the C language and offers object-oriented programming options and a unique strategy to reminiscence allocation.
The main distinction between C and C++ is that C++ supplies object-oriented options no longer to be had within the authentic model of the language, corresponding to categories, strategies, digital purposes, and many others.; this permits programmers to create extra tough code with knowledge abstraction and encapsulation, which may make it more uncomplicated to take care of and reuse code; whereas this larger point of abstraction could make it harder for rookies or those that should not have an figuring out of those ideas.
48. Point out the structural distinction between the bitmap and b-tree index?
A bitmap index is an indexing construction this is used on massive tables with many rows. The bitmap index is a desk that retail outlets one row for every key within the desk. The rows are ordered by means of the important thing worth, and the column values of every row constitute the selection of instances this key seems within the desk. Bitmap indexes are used to briefly in finding all keys with a given worth or vary of values.
A B-tree index is an indexing construction that retail outlets knowledge taken care of on a number of columns. The knowledge could also be saved internally as a B-tree, which can also be searched successfully by means of scanning from left to all over adjoining nodes at every point till the specified access is located, or it can be saved as an exterior record wherein case it may be scanned sequentially from starting to finish.
49. Differentiate between socket and consultation?
A socket is an object this is used to ship and obtain knowledge throughout a community. This is a explicit example of an endpoint this is used to facilitate verbal exchange between two computer systems. A socket can also be one-way or two-way. A consultation is verbal exchange between two computer systems.
50. What’s an array?
An array is a selection of knowledge that may be accessed by means of identify. It’s very similar to a listing, however arrays have a selected order.
Arrays are a commonplace knowledge construction in programming. They will let you retailer a selection of gadgets in one location.
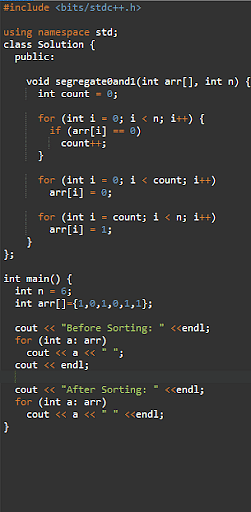
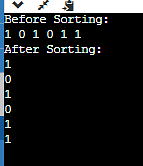
51. If you’re given an array of 1s and 0s, how are you able to organize the 1s and 0s in combination in one array scan? Optimize the boundary prerequisites.
We will use a two pointer means for arranging the array in one array scan. Our function is to attenuate the selection of steps had to scan all the array in every case.
Output –
52. Outline knowledge abstraction. What’s their significance?
Information abstraction is the most important idea in laptop science. It’s used to cover the main points of an implementation from the customers of that implementation. Information abstraction is used to create interfaces which are simple to make use of and perceive. It is usually used to make code extra modular and more uncomplicated to take care of.
53. Point out a serve as to switch two numbers with out the usage of a brief variable.
Output –

54. What’s reminiscence allocation in C/C++?
Reminiscence allocation is a procedure in which a pc program requests a certain quantity of reminiscence from the running device. The method of allocating this reminiscence is referred to as dynamic reminiscence allocation. This text will give an explanation for methods to allocate reminiscence in C/C++. Allocating reminiscence is necessary as it means that you can retailer knowledge that you want to make use of afterward on your program.
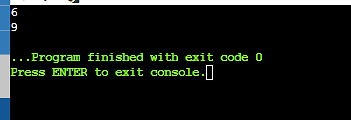
55. Write output of the programme?
Program to print the Nth quantity within the collection.
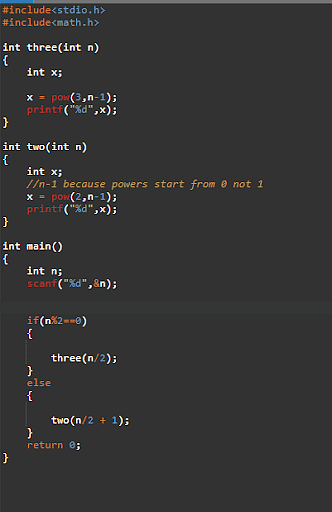
Output-
56. Outline digital serve as and natural digital serve as.
Ans. Digital purposes and natural digital purposes are necessary facets of device building. They enable a device developer to summary away explicit main points of an set of rules. This abstraction makes the code extra readable and maintainable.
digital purposes and natural digital purposes are a kind of serve as. They’re referred to as digital as a result of they don’t have a bodily location in this system. As a substitute, they’re saved in reminiscence.
57. What are WPF and WCF?
Ans. WPF and WCF are two necessary applied sciences used within the .NET Framework. WPF is a platform-independent GUI building framework that used to be offered in Home windows Vista. WCF is a era that permits you to create and organize products and services.
WPF and WCF are two well-liked frameworks used for construction Home windows-based device. WPF is a consumer interface framework, whereas WCF is a provider framework. They each permit builders to create cross-platform programs.
58. Which programming languages are very important to the TCS campus interview?
Necessary programming languages for the TCS campus interview are:
- C programming
- C++ programming
- Java programming
59. How is C other from C?
C is a superset of C. Main added options in C come with Object-Orientated Programming, Exception Dealing with, and a wealthy C++ library.
60. Is the C platform self sufficient?
C is a platform-dependent language. Which means that methods written in C will best run at the platform for which they had been compiled. Platforms can also be any aggregate of {hardware} and running device, corresponding to Home windows, macOS, Linux, or Android. Whilst C isn’t strictly transportable throughout all platforms, it’s imaginable to write down code this is transportable between other platforms.
61. What are constructions in C?
Resolution: A construction is a user-definable knowledge sort in C/C++. It means that you can workforce positive kinds of data right into a unmarried variable.
62. Provide an explanation for inheritance in OOPS
Object-oriented programming considers inheritance to be a mechanism in response to categories. Inheritance refers to inheriting knowledge contributors and purposes of a mum or dad category to a kid category. A category acquired from upper ranges is known as a kid category, and the top-level category from which the kid category is acquired is known as a sub-class.
63. What 4 ideas does OOPS adhere to?
The 4 elementary ideas of object-oriented programming programs are abstraction, inheritance, encapsulation, and polymorphism.
64. What prevents Java from being a purely object-oriented language?
Java helps a number of the OOPs ‘ complicated OOPs houses, together with Inheritance, Encapsulation, Polymorphism, Abstraction, and so much others, however nonetheless misses a couple of of them. Because of this, it is not a natural OOPs language.
65. What distinguishes a clustered index from a non-clustered index?
Clustered index is an index that reorders tables in some way that is sensible for the knowledge. Nonclustered index is an index wherein the logical order of the index does no longer fit the bodily order of the rows on disk.
66. What does a clear knowledge control device point out?
The clear database control device is a kind of database control device (DBMS) that hides its bodily construction from customers. The bodily construction or bodily garage construction refers back to the reminiscence of a device, and it describes how knowledge is saved on a disk.
67. What are you aware concerning the spine community?
A spine community is continuously a centralized device that distributes other routes and knowledge to more than one networks. It additionally handles the control of bandwidth on quite a lot of channels.
supply: www.simplilearn.com












