Amazon Internet Products and services (AWS) cloud supplies a protected digital platform the place customers can deploy their packages. In comparison to an on-premises atmosphere, AWS safety supplies a top stage of information coverage at a lower price to its customers. There are lots of forms of safety services and products, however Identification and Get entry to Control (IAM) is one probably the most extensively used. AWS IAM allows you to securely regulate get right of entry to to AWS services and products and assets in your customers. The usage of IAM, you’ll create and organize AWS customers and teams, and use permissions to permit and deny their get right of entry to to AWS assets.
Allow us to start this AWS IAM educational through working out AWS safety.
What’s AWS Safety?
Cloud safety is the best possible precedence in AWS. While you host your atmosphere within the cloud, you’ll be confident that it’s hosted in a knowledge heart or in a community structure that’s constructed to satisfy the necessities of probably the most security-sensitive group. Moreover, this top stage of safety is to be had on a pay-as-you-go foundation, that means there’s actually no prematurely value, and the fee for the usage of the provider is so much less expensive in comparison to an on-premises atmosphere.
There are lots of forms of safety services and products to be had however a few of them are extensively utilized by AWS, corresponding to:
- IAM
- Key Control Device (KMS)
- Cognito
- Internet Get entry to Firewall (WAF)
We will take care of IAM on this educational.
IAM allows you to organize get right of entry to to AWS services and products and assets in an excessively protected method. With IAM you’ll create teams and make allowance the ones customers or teams to get right of entry to some servers, or you’ll deny them get right of entry to to the provider.
Why IAM?
Prior to AWS or IAM, passwords have been continuously shared in company environments in an excessively insecure method: over the telephone or via electronic mail. Ceaselessly just one admin password existed, which used to be often saved in a suite location, or there used to be just one one who may just reset it, and also you had to name the individual to invite for the admin password over the telephone. That used to be no longer protected in any respect, as a result of any one may just stroll through and eavesdrop after which stroll away with the password and get right of entry to in your device and data.
As of late we’ve got a extra protected verbal exchange software: a third-party software referred to as Slack, which is hosted on AWS. It is helping other people to percentage a file throughout the software in order that eavesdropping is eradicated.
Within the subsequent phase of the AWS IAM educational, allow us to perceive what IAM is.
What’s IAM?
AWS Identification and Get entry to Control (IAM) is a internet provider for securely controlling get right of entry to to AWS assets. It allows you to create and regulate services and products for person authentication or prohibit get right of entry to to a undeniable set of people that use your AWS assets.
How Does IAM Paintings?
The IAM workflow contains the next six components:
- A important is an entity that may carry out movements on an AWS useful resource. A person, a job or an software is usually a important.
- Authentication is the method of confirming the identification of the important looking to get right of entry to an AWS product. The important will have to supply its credentials or required keys for authentication.
- Request: A important sends a request to AWS specifying the motion and which useful resource must carry out it.
- Authorization: Via default, all assets are denied. IAM authorizes a request provided that all portions of the request are allowed through an identical coverage. After authenticating and authorizing the request, AWS approves the motion.
- Movements are used to view, create, edit or delete a useful resource.
- Assets: A suite of movements may also be carried out on a useful resource similar in your AWS account.
Allow us to discover the parts of IAM within the subsequent phase of the AWS IAM educational.
Elements of IAM
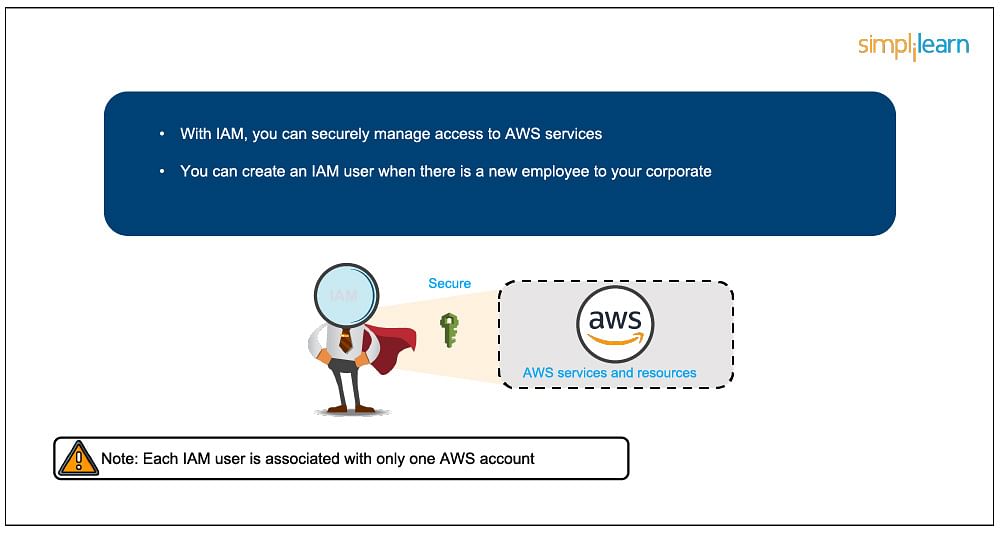
There are different elementary parts of IAM. First, we’ve got the person; many customers in combination shape a gaggle. Insurance policies are the engines that permit or deny a connection in response to coverage. Roles are transient credentials that may be assumed to an example as wanted.
An IAM person is an identification with an related credential and permissions connected to it. This may well be a real one who is a person, or it may well be an software that may be a person. With IAM, you’ll securely organize get right of entry to to AWS services and products through growing an IAM person title for every worker for your group. Each and every IAM person is related to just one AWS account. Via default, a newly created person isn’t licensed to accomplish any motion in AWS. The good thing about having one-to-one person specification is that you’ll in my opinion assign permissions to every person.
A choice of IAM customers is an IAM workforce. You’ll be able to use IAM teams to specify permissions for more than one customers in order that any permissions implemented to the gang are implemented to the person customers in that workforce as smartly. Managing teams is rather simple. You put permissions for the gang, and the ones permissions are robotically implemented to all of the customers within the workforce. When you upload some other person to the gang, the brand new person will robotically inherit all of the insurance policies and the permissions already assigned to that workforce. This lessens the executive burden.
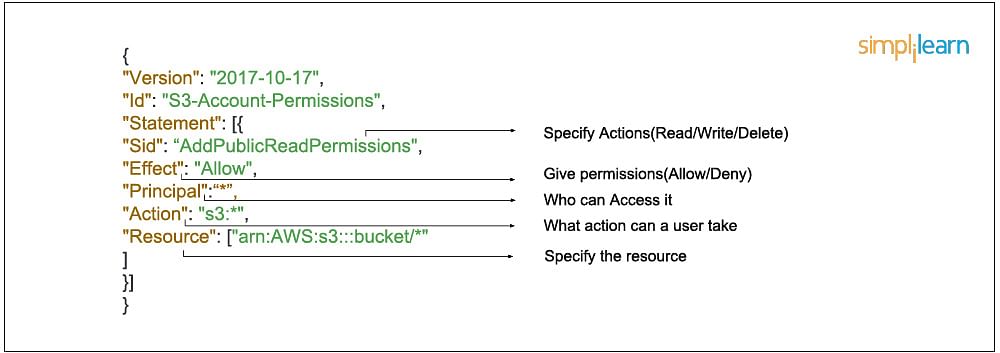
An IAM coverage units permission and controls get right of entry to to AWS assets. Insurance policies are saved in AWS as JSON paperwork. Permissions specify who has get right of entry to to the assets and what movements they may be able to carry out. For instance, a coverage may just permit an IAM person to get right of entry to one of the vital buckets in Amazon S3. The coverage would comprise the next knowledge:
- Who can get right of entry to it
- What movements that person can take
- Which AWS assets that person can get right of entry to
- When they may be able to be accessed
In JSON structure that might appear to be this:
There are two forms of insurance policies: controlled insurance policies and inline insurance policies.
- A controlled coverage is a default coverage that you just connect to more than one entities (customers, teams, and roles) for your AWS account. Controlled insurance policies, whether or not they’re AWS-managed or customer-managed, are stand-alone identity-based insurance policies connected to more than one customers and/or teams.
- Inline insurance policies are insurance policies that you just create which can be embedded immediately right into a unmarried entity (person, workforce or position).
An IAM position is a suite of permissions that outline what movements are allowed and denied through an entity within the AWS console. It’s very similar to a person in that it may be accessed through any form of entity (a person or AWS provider). Function permissions are transient credentials.
For instance, chances are you’ll need to permit a cell app to make use of AWS assets, however you do not need it to avoid wasting the important thing, credential or password. Or chances are you’ll need to give get right of entry to to assets to a person who already has an identification outlined outdoor of AWS, corresponding to a person who already has Google or Fb authentication. If you wish to supply any individual with a provider or let any individual get right of entry to assets for your account, you’ll use roles for that objective too. You additionally may need to grant transient get right of entry to in your account to a 3rd get together, corresponding to a expert or an auditor. They’re no longer everlasting customers, simply customers with transient get right of entry to in your atmosphere.
Allow us to discover the options of IAM within the following phase of the AWS IAM educational.
Options of IAM
To check, listed here are one of the crucial major options of IAM:
- Shared get right of entry to to the AWS account. The principle characteristic of IAM is that it lets you create separate usernames and passwords for particular person customers or assets and delegate get right of entry to.
- Granular permissions. Restrictions may also be implemented to requests. For instance, you’ll permit the person to obtain knowledge, however deny the person the power to replace knowledge throughout the insurance policies.
- Multifactor authentication (MFA). IAM helps MFA, through which customers supply their username and password plus a one-time password from their telephone—a randomly generated quantity used as an extra authentication issue.
- Identification Federation. If the person is already authenticated, corresponding to via a Fb or Google account, IAM may also be made to accept as true with that authentication manner after which permit get right of entry to in response to it. This may also be used to permit customers to handle only one password for each on-premises and cloud atmosphere paintings.
- Unfastened to make use of. There’s no further price for IAM safety. There’s no further price for growing further customers, teams or insurance policies.
- PCI DSS compliance. The Cost Card Trade Knowledge Safety Usual is a knowledge safety usual for organizations that deal with branded bank cards from the key card schemes. IAM complies with this usual.
- Password coverage. The IAM password coverage lets you reset a password or rotate passwords remotely. You’ll be able to additionally set regulations, corresponding to how a person must select a password or what number of makes an attempt a person would possibly make to supply a password prior to being denied get right of entry to.
Within the final phase of the AWS IAM educational, allow us to undergo a demo on how you can create an S3 bucket the usage of the multifactor authentication (MFA) characteristic.
Demo: Create an S3 Bucket The usage of the MFA Function
The general phase of this newsletter places in combination the entire knowledge introduced and makes use of it to unravel a elementary drawback.
Downside commentary: To create an S3 bucket for a corporation through which every person can learn and write knowledge with multifactor authentication.
Process: To create insurance policies and assign permissions for a person and a gaggle.
- Supply get right of entry to (learn and write) to the developer workforce.
- Supply a coverage through which a person is permitted to learn or denied permission to jot down an object in an S3 bucket.
It is a excellent use case you probably have touchy knowledge in an S3 bucket and you need handiest privileged or MFA-authenticated customers to make adjustments to these buckets. For the ones privileged customers, you possibly can allow multifactor authentication.
Conclusion
The ideas supplied on this AWS IAM educational gave you a transparent concept of AWS safety and IAM. Amazon Internet Products and services provides many far flung computing services and products aside from safety services and products. As corporations internationally are adopting AWS Cloud, there can be an enormous call for for pros who’ve in-depth wisdom of AWS ideas and services and products. Simplilearn makes it simple so that you can improve your self and achieve experience in AWS throughout the Cloud Architect Route. Get began nowadays and excel within the box of Amazon Internet Products and services.
The AWS Answer Architect Certification delves deeply into the an important sides of AWS Identification and Get entry to Control (IAM), an very important provider for managing safety in AWS environments. This certification emphasizes the significance of working out IAM’s complete options for controlling get right of entry to to AWS services and products and assets securely.
supply: www.simplilearn.com












